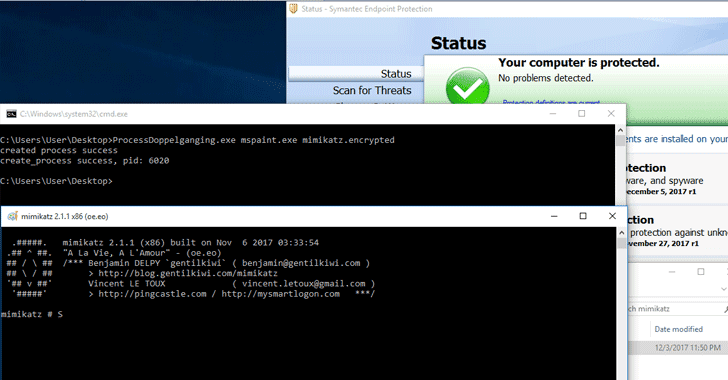
In addition, it even works on all the versions of the tech giant Microsoft’s Windows operating systems. Hence, in this article, we will give you all the keys of “Process Doppelgänging”. This new security threat is dubbed as “Process Doppelgänging”, this new code injection technique simply takes the advantage of a native Windows function and an outdated implementation to load processes. The group of researchers who is responsible for this discovery have presented their discovery during the Black Hat 2017 security conference which was held in the city of London, United Kingdom.
The new security threat which is dubbed as “Process Doppelgänging” simply helps to skip the security measures of Windows antivirus
As explained, Process Doppelgänging is capable of attacking all modern versions of the tech giant Microsoft’s Windows operating system. This implies that it is capable of compromising security from Windows Vista to Windows 10. The head of the research points out that its operation is similar to that of the Process Hollowing technique used years ago to bypass the mitigation functions of the main security solutions. At this time, all modern antivirus programs have been updated so that Process Hollowing does not help, so it has had to look for another approach to achieve the similar technique. In this case, we have Process Doppelgänging that “abuses” the Windows NTFS Transactions and that outdated implementation of Windows that was designed at the time for Windows XP but has now gone and modded itself from version to version. In the tests carried out, they have managed to successfully skip the security measures imposed by Windows Defender, Kaspersky Labs, ESET NOD32, Symantec, Trend Micro, Avast, McAfee, AVG, Panda or tools such as Volatility. In Windows 7 Service Pack 1, Windows 8.1 and Windows 10 has proven its operation. Of course, we must make it clear that they have not been able to skip the security of the antivirus in Windows 10 Fall Creators Update because the use of this technique caused an error and the subsequent appearance of the famous blue screen of death. Interestingly, the tech giant Microsoft recently patched this problem, so it is possible for Process Doppelgänging to work again even in these versions. Although an immediate response from the tech giant Microsoft is not expected by launching an emergency security patch, it would be advisable that the main security solutions, with the antivirus at the head, launch updates to eliminate this technique. So, what do you think about this new security threat? Simply share all your views and thoughts in the comment section below.