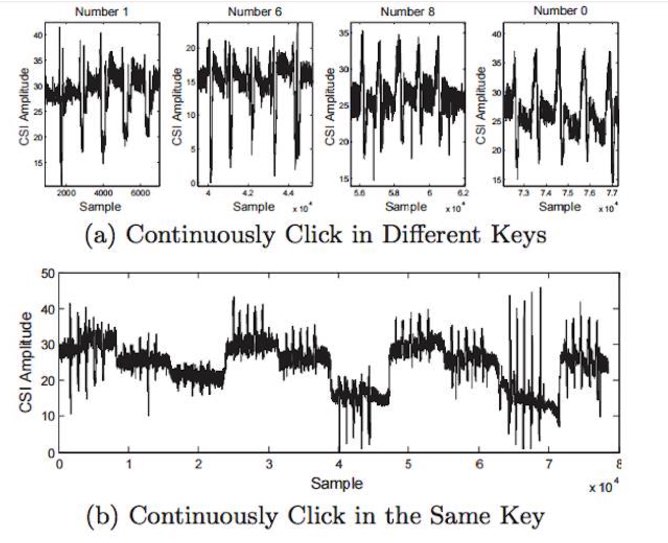
In one of the recent development, a group of researchers has developed WindTalker. Researchers at the Jaio Tong University in Shanghai, The University of Massachusetts and the University of South Florida found a way to steal credentials of Smartphone user without infecting their machines with malware. Actually, how we move our fingers across our phone’s touchscreen alters the Wifi signals transmitted by a smartphone which causes interruptions that any hacker can intercept, analyze and can even reverse engineer to guess what you just typed on your phone or in the password fields. Researchers have published the whole details of WindTalker which is named as When CSI Meets Public WiFi: Inferring Your Mobile Phone Password via WiFi signals, here “CSI” means channel state information. The researchers use a technique that is used only in modern WLAN routers because it relies on the sophisticated beam-forming implemented in Multiple-Input, Multiple-Output (MIMO) antenna configurations. This technique is used to optimally align the WLAN signal to the receiving device in multi-antenna routers, thus increasing the data throughput. In such a system, the gestures of hands and fingers on the touch screen cause minute changes in the signal strength of the WLAN signals of the multiple antennas, which can be read from the values of the CSI. Depending on which virtual key is pressed, the researchers are able to detect characteristic changes of the CSI from which an attacker could assume the key input. To carry out this type of attack, an attacker doesn’t need to compromise the target. The attacker can steal the passwords with the help of a malicious WiFi hotspot. Here’s an image of CSI values of a user who repeatedly clicks on the same button. The researchers also suggested ways to block WindTalker attacks. They wrote that randomizing the keypad layouts can prevent you from WindTalker attacks. If you need to find out more information about this then you could find it on the research paper.