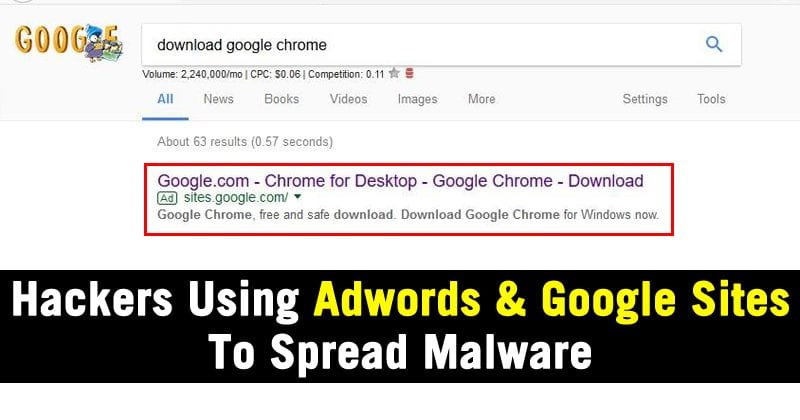
To be more precise, cyber offenders have helped the Google Chrome web browser to get the user to install the threat in question. The security experts indicate that the installer groups several programs classified as PUP (Potentially Unwanted Programs). Some of these are responsible for listening to the waiting for instructions from a remote server. All those who do not know Google AdWords, it is an ad service. The user pays an amount to show his ad in the results of the search engine of the US company. That is, if we want to look for something related to “networks” or “routers”, the first result will be an advertisement about the purchase of products related to networks. Where is the trick? If the user searches for “Google Chrome”, they will always choose to download the first search result. Many users are not aware that this content is an advertisement. This makes one practice clear: the tech giant Google does not have a thorough analysis of the content that appears in these ads. Cybercriminals are paying the Internet Giant, Google for distributing access to a web page that allows malware to be downloaded. It must also be said that the content shown in these “results” depends to a large extent on the searches and cookies generated on the computer that the user is using. But the problem does not end here for the Mountain View company.
In addition to Google AdWords, cybercriminals also use Google Sites
It is one of the many tools offered through G Suite. It allows the creation of web pages in a simple way. This causes cybercriminals to create a false page to download the Google Chrome web browser. The users think that it is a legitimate location and they continue with the process. The file that is downloaded has the name ChromeSetup.exe. This file is downloaded from a Google Drive folder. Yes, oddly enough, from Google to offer the full support to carry out a distribution of malware.
The executable contains the threat Coinrobot.xyz
Although it is not well known, it is a malware that installs coin mining software on the user’s computer using hardware resources. It goes without saying that only computers with a Windows operating system are likely to be affected. As can be seen, until recently the desire was to carry out the encryption of the files and request a reward. Now it is to carry out the mining of cryptocurrencies. The Internet Giant Google is already warned about this practice. Luckily for users, the threats included in the fake Google Chrome installer are detected by most security tools, even before they run. So, what do you think about this? Simply share your views and thoughts in the comment section below.
Δ