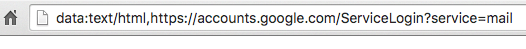
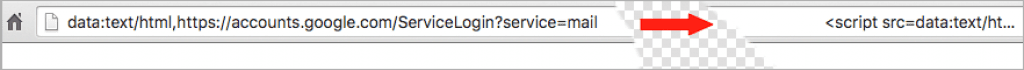
The hacker here compromises a victim’s Gmail account, and after gaining the full access of Gmail account, they start rifling through inboxes to launch subsequent attacks to spread the attack. Hackers have used some tricky way to initiate the attack, and hackers first look for an attachment that victims have sent to their contacts then they gather all the contacts and sends them an image (screenshot) of that attachment and include it in reply to the sender with the same or relevant subject for the email. What makes this phishing campaign successful is the phishing emails come from someone the victim knows. Once the victim clicks on the image, expecting Gmail to give them a preview of the attachment. Instead, a new tab opens up which prompts users to Sign-in with Google account once again. It’s a TRAP! The subdomain of the Fake Gmail login page is accounts.google.com, which is enough to fool the majority of Gmail users into believing that they are on a legitimate Google Page. WordFence CEO Mark Maunder who reported the phishing campaign wrote in a blog post: “This phishing technique uses something called a ‘data URI’ to include a complete file in the browser location bar. When you glance up at the browser location bar and see ‘data:text/html…..’ that is actually a very long string of text.” “In this [attack] the ‘data:text/html’ and the trusted hostname are the same color. That suggests to our perception that they’re related and the ‘data:text/html’ part either doesn’t matter or can be trusted.” So, make sure you are login through a legitimate Google page, and enabling two-factor authentication will make sure you don’t fall into this trap. So, what you think about this? Share your thoughts on the comment box below.
Δ